Managed IT support and cybersecurity services in Canberra
Welcome to Care Managed IT - Managed IT Support Canberra
Maximise Business Efficiency with CareMIT's Managed IT Services in Canberra
At CareMIT, we specialise in delivering exceptional managed IT support and cybersecurity services in Canberra, tailored to the unique needs of your business. Our proactive approach to IT and security management ensures your infrastructure is robust, secure, and strategically aligned with your business goals, enabling you to focus on core operations with complete peace of mind.
Our unique ACTION Plan forms the foundation of our service delivery, enabling us to meticulously Assess your IT requirements, Create custom solutions, Test for optimal performance, Implement seamlessly, Oversee for maximum efficiency, and Navigate future IT challenges to ensure continuous improvement and development.
In today’s fast-paced digital landscape, maintaining an agile, efficient, and secure IT infrastructure is crucial. At CareMIT, we understand the complexities of managing IT while driving business growth. As your trusted Managed Service Provider (MSP) and Managed Security Service Provider (MSSP), we aim to transform IT management from a potential burden into a strategic advantage.
Our process begins with a comprehensive assessment of your current IT environment. We then create and rigorously test a customised solution designed to meet your specific needs. After fine-tuning, we implement the solution and continuously oversee its performance, ensuring your IT and security systems remain at their peak.
But our commitment doesn’t stop there. We proactively navigate emerging IT challenges to foster continuous improvement and adaptability. By choosing CareMIT for your IT and security management, you can concentrate on scaling your business with confidence.
We provide proactive solutions that not only maintain your IT infrastructure but also enhance your business momentum, safeguarding your data against the latest security threats. With CareMIT, your IT becomes a strategic asset, not just a necessity.
Experience Peace of Mind with Expert IT Management
Partner with CareMIT to enjoy a seamless, secure, and efficient digital journey. Let’s redefine your IT experience and drive your business forward together.
How secure do you think you are?
Learn a little more about how safe your business is with these free resources
Do the AUDIT and Get a FREE Book!
The question in this audit are designed to give you a starting point (baseline) to build security in depth.
Complete these 30 simple yes / no questions and get your personalized report in your inbox within minutes.
Discover your strengths and weaknesses and use your A.C.T.I.O.N. Plan to make data-driven decisions.
Is Your Managed IT Support and Cybersecurity Provider Helping You Grow?
Your managed IT support and cybersecurity provider should empower your business to increase revenue, adapt to changes, and boost productivity. Are they doing this for you? Or are they insisting on a one-size-fits-all approach that stifles your uniqueness, turning you into just another business clone?
If your provider is not meeting your needs, it might be time for a change.
At CareMIT, we offer a limited number of FREE 57-point third-party system audits. These audits identify potential issues in your business infrastructure and security posture, ensuring you are protected against emerging cyber threats.
We work with business owners, managers, C-suite executives, and board members who are committed to protecting their organisations from cyber incidents. If you understand the need for expert guidance and want to make a meaningful impact in your community, we are here to help.
Our specialised Cybersecurity ACTION Plan is designed for nonprofit organisations and SMEs, offering a holistic approach to security. This plan helps management teams:
- Understand the critical importance of asset management.
- Implement essential controls and management features.
- Foster a positive environment for their teams.
- Ensure all systems are correctly integrated.
- Develop operational resilience to recover swiftly from disruptions.
- Embrace innovation as it becomes viable.
Take the Next Step Towards a Secure Future
Book a time to discover how CareMIT can help protect your organisation and drive its growth. Let’s secure your business, together.
Book a time to ask how Care MIT can help you!
Sign up for your monthly newsletter.
Whether you are looking for a done-for-you solution to cybercrime or need help with your onsite team, Care MIT is passionate about implementing the correct security in-depth solution to suit your needs.
At Care MIT we design managed IT Support and cybersecurity solutions to protect your organisation that allows your organisation to prosper but are not based on tick-box compliance and governance.
I am Roger Smith, your Virtual CISO

In 2011, I became a target of cybercrime. Despite having nearly 20 years of experience in IT, this experience was a wake-up call. It made me realise that if I could be targeted, what chance do everyday people have to protect themselves?
This led me to dive deep into understanding how cybercriminals operate and to use that knowledge to shape what CareMIT does today: protecting our clients' businesses from cyber threats.
Cybersecurity Doesn't Have to Be Complicated.
At its core, cybersecurity is about staying one step ahead of cybercriminals. To achieve this, you must be proactive, focused on the details, and equipped with a solid strategy. That's where our Cybersecurity A.C.T.I.O.N Plan comes in.
We simplify the complexities of the digital world by implementing proven cybersecurity strategies that do more than just protect your organisation—they empower you to adapt, grow, and remain resilient in the face of threats.
Whether you want to take charge with our guidance and framework or let us handle it for you with the expertise we've built over the last decade, CareMIT is here to support you every step of the way.
LETS TALK
How Do You Know if Your Business Security is Effective?
Many business owners gauge their security success by thinking, "We haven’t had a cyber incident… yet."
Unfortunately, this mindset is flawed given the evolving tactics of today's cybercriminals.
To effectively counteract cyber threats, your business security strategy must encompass the following:
- Identify and Protect Critical Assets: Know what needs protection and put the right safeguards in place.
- Implement Essential Controls: Establish robust management practices and security controls to protect your business.
- Empower Your Team: Equip your staff with the tools and training they need to recognize and respond to potential threats.
- Ensure Seamless Integration: Create systems that communicate effectively with each other and the people who use them.
- Build Resilience: Develop the ability to recover quickly from incidents while documenting actions taken for future improvement.
- Adopt Innovative Solutions: Stay ahead of cyber threats by incorporating cutting-edge technologies as they become available.
The Cybersecurity A.C.T.I.O.N. Plan is designed to address all these critical areas, ensuring your business stays secure in a rapidly changing digital landscape.
Why CareMIT is Your Premier Choice for Business Security Solutions
What Makes CareMIT So Remarkable?
At CareMIT, we go above and beyond to ensure our clients are as secure as possible. Our commitment to your business includes:
- Unmatched Client Protection: We provide every client with a tested and proven strategy to swiftly restore normal operations in the event of a disruption, minimizing downtime and impact.
- Risk-Free Satisfaction: We stand by our services with a 30-day money-back guarantee, giving you confidence in everything we do.
- Community Impact: We actively support digital inclusion by helping underserved communities enter the digital world safely and securely.
- Enhanced Digital Security: We guarantee that your business will be ten times more secure against digital attacks once you become our client.
Choose CareMIT and experience security solutions that go beyond the ordinary.ere before you became a client
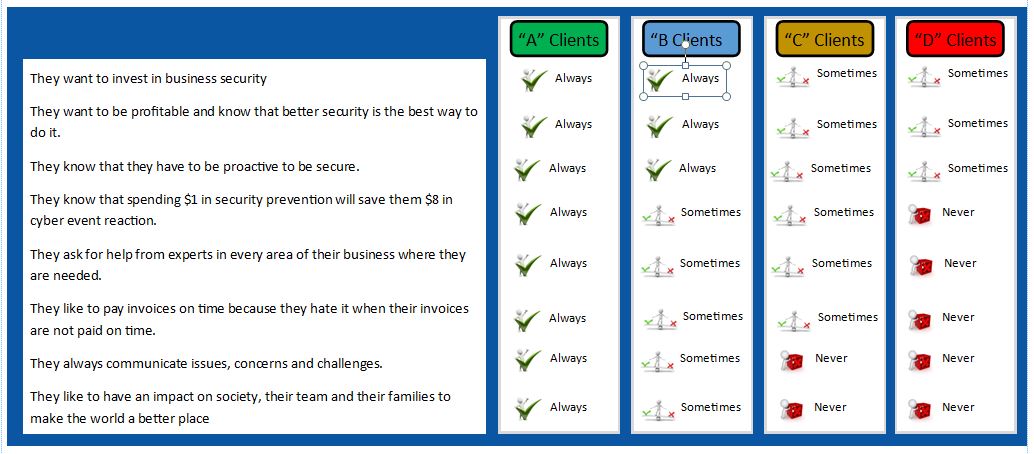
Our ideal clients are "not-for-profit organisations, associations, charities and small and medium businesses" that want to.
-
Allow their resources to go further in protecting their organisation.
-
Have a systematic way of implementing and managing security requirements.
-
Increase their capability to survive a cyber event.
-
Work within a cybersecurity framework that increases security but saves money and decreases the chance of a cyber event
Recent Posts
-
Changing the Narrative, Do Victims Of Cybercrime Deserve Our Support
-
The Critical Need for Cybersecurity Specialists in Leadership
-
Cultivating a Forward-Thinking Partnership with Your MSP
-
Cyber Strategies for SMEs and Nonprofits
-
Fearmongering in Cybersecurity – From Tactic to Necessity
-
How to Secure Your Network with Distributed Teams for SMEs and Nonprofits
-
The Murky Waters of False Cyber Breach Claims
-
Prevention, the New Paradigm in Risk Management for SMEs and Non-Profits
-
The Art and Science of Cyber Resilience
-
Your Digital Footprint – Permanence, Accessibility, and Implications
To register for your free 57 point business infrastructue and cybersecurity audit, complete the following form and we will organize a convenient time.
Giving Back
By working with Care MIT Pty Ltd you are helping to give back to the world community.
Running a business for almost 2 decades takes a special kind of person, someone who can delegate, manage, be inclusive and give back. Care MIT Pty Ltd is more than a business, it’s a team and a family which extends to our clients too. As part of the Care MIT family, in November 2021 we joined B1G1 – Business for Good; to help make a difference while doing what we normally do.
If you are a client then every time that you pay our bill on time we donate 5 hours' worth of technical support and internet access to students in Uganda.

